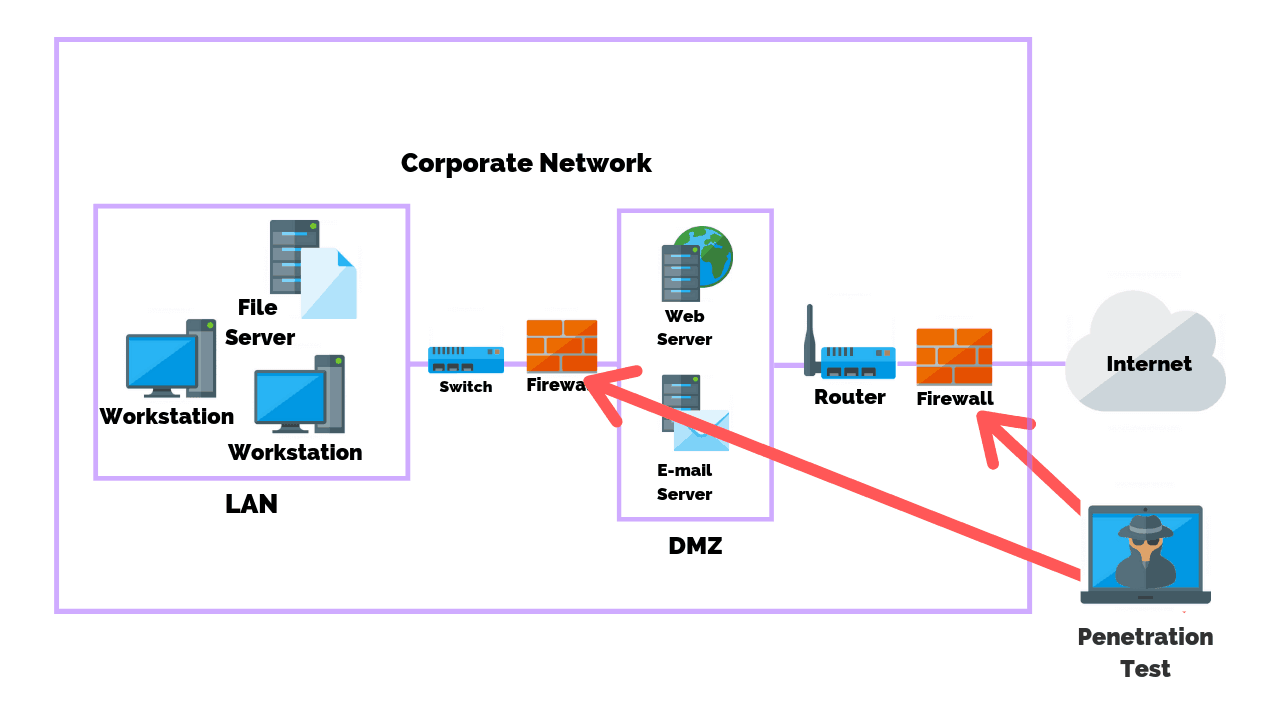
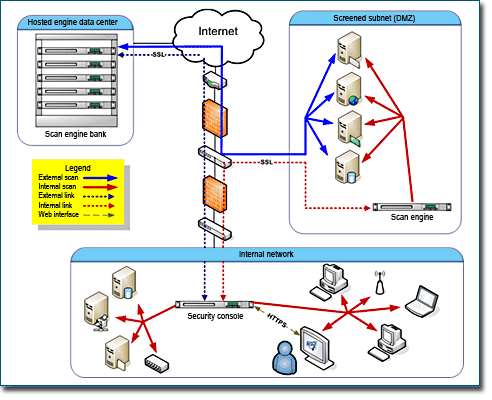
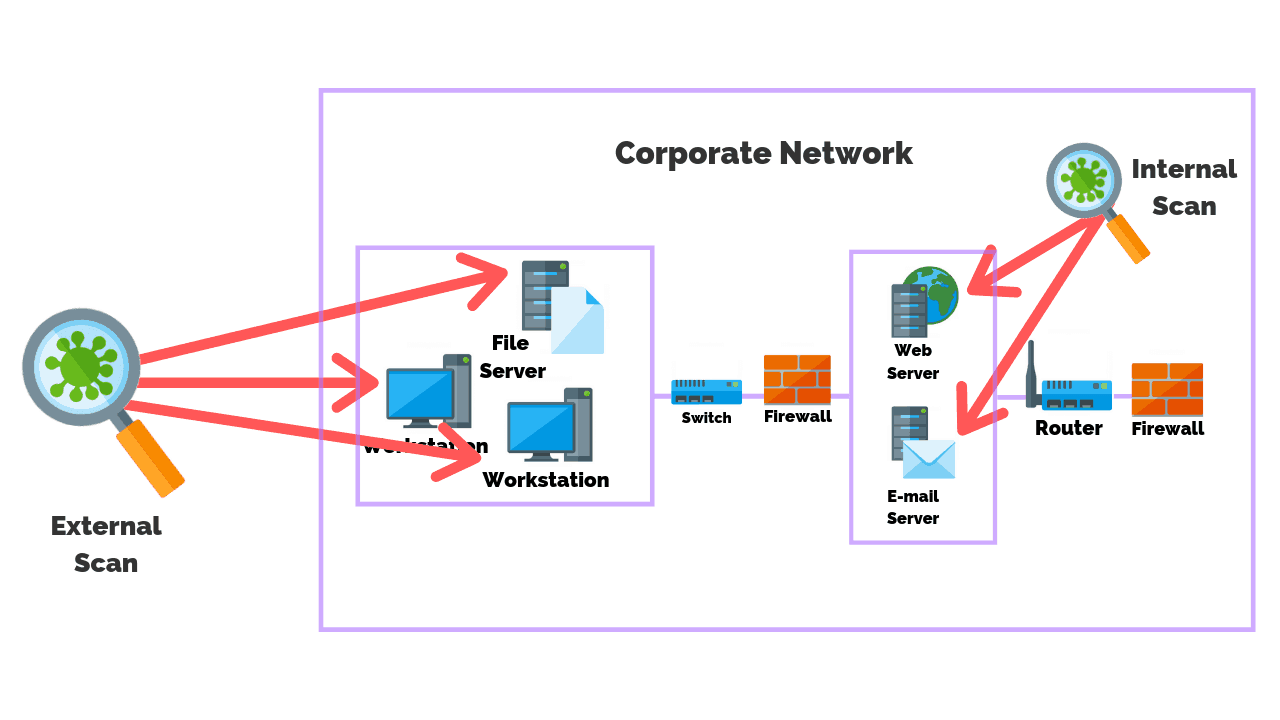
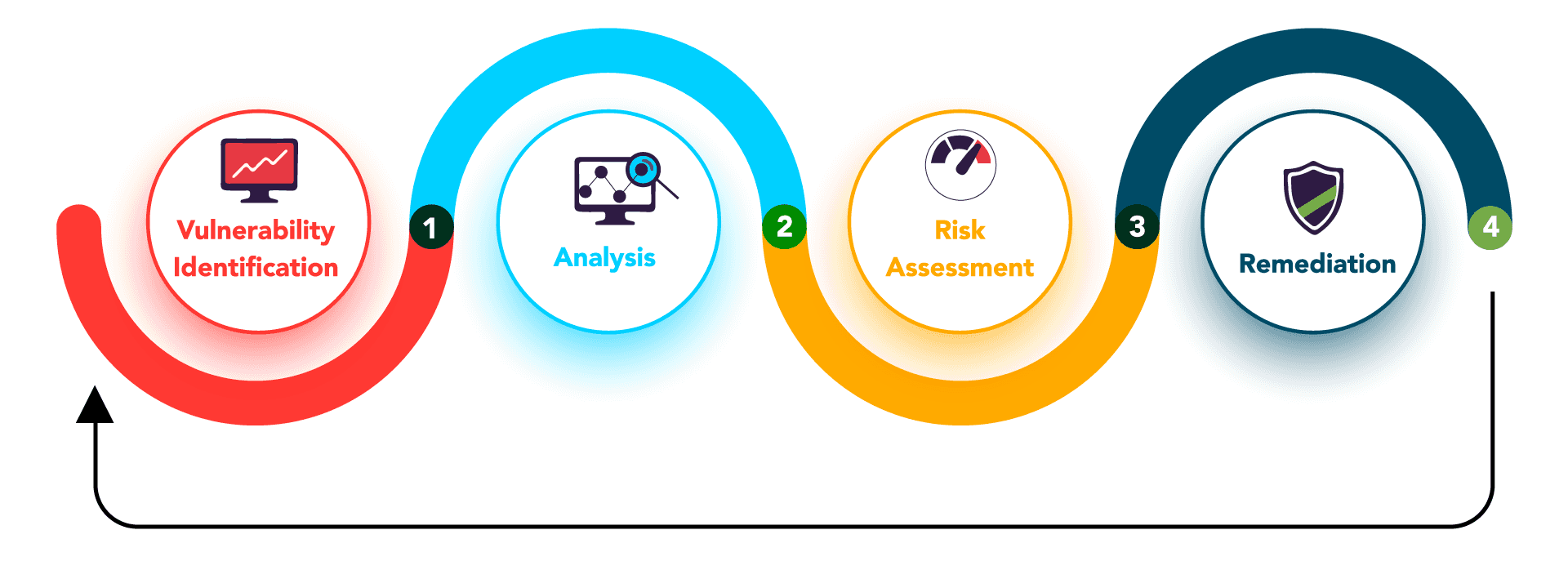
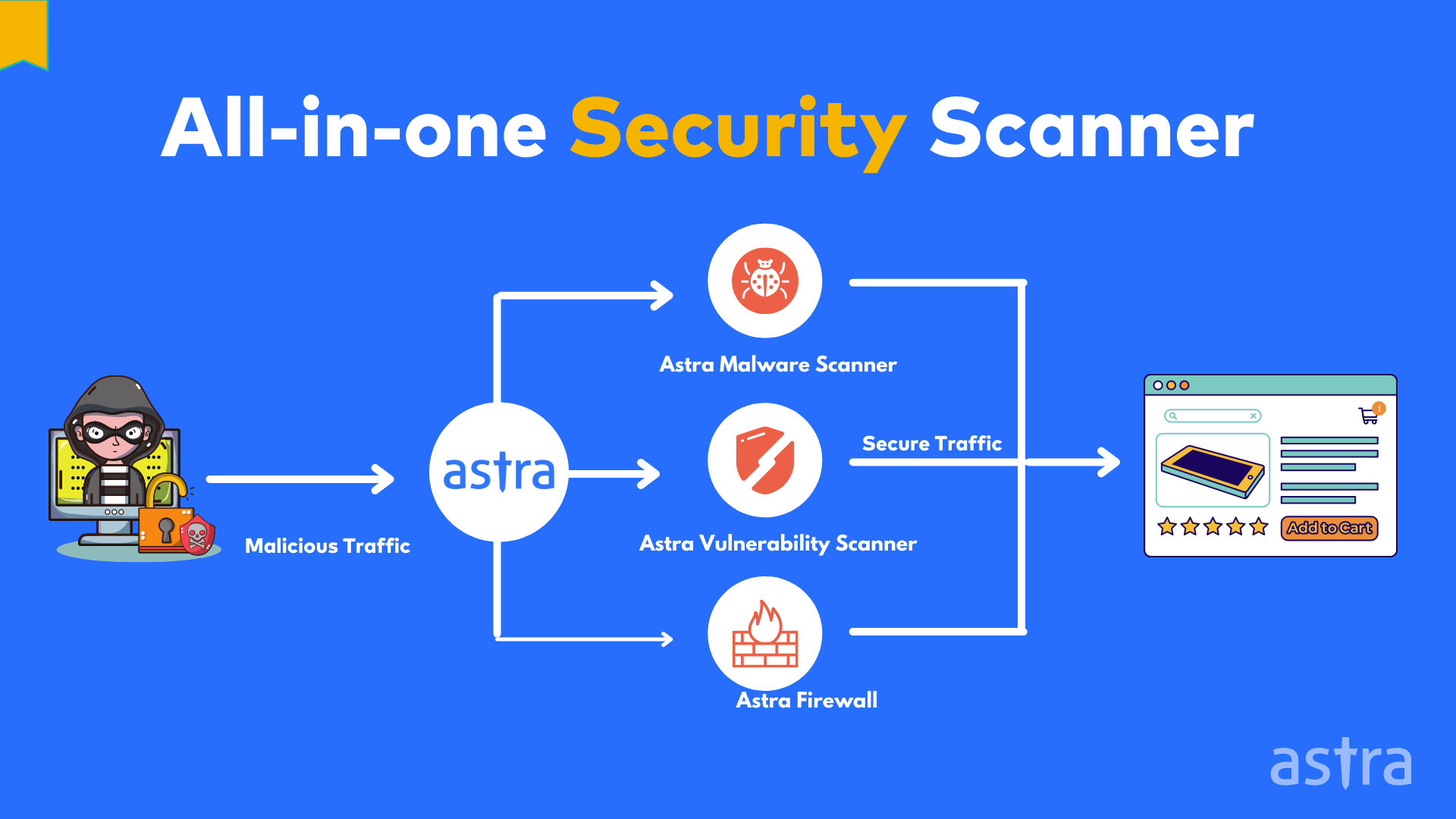
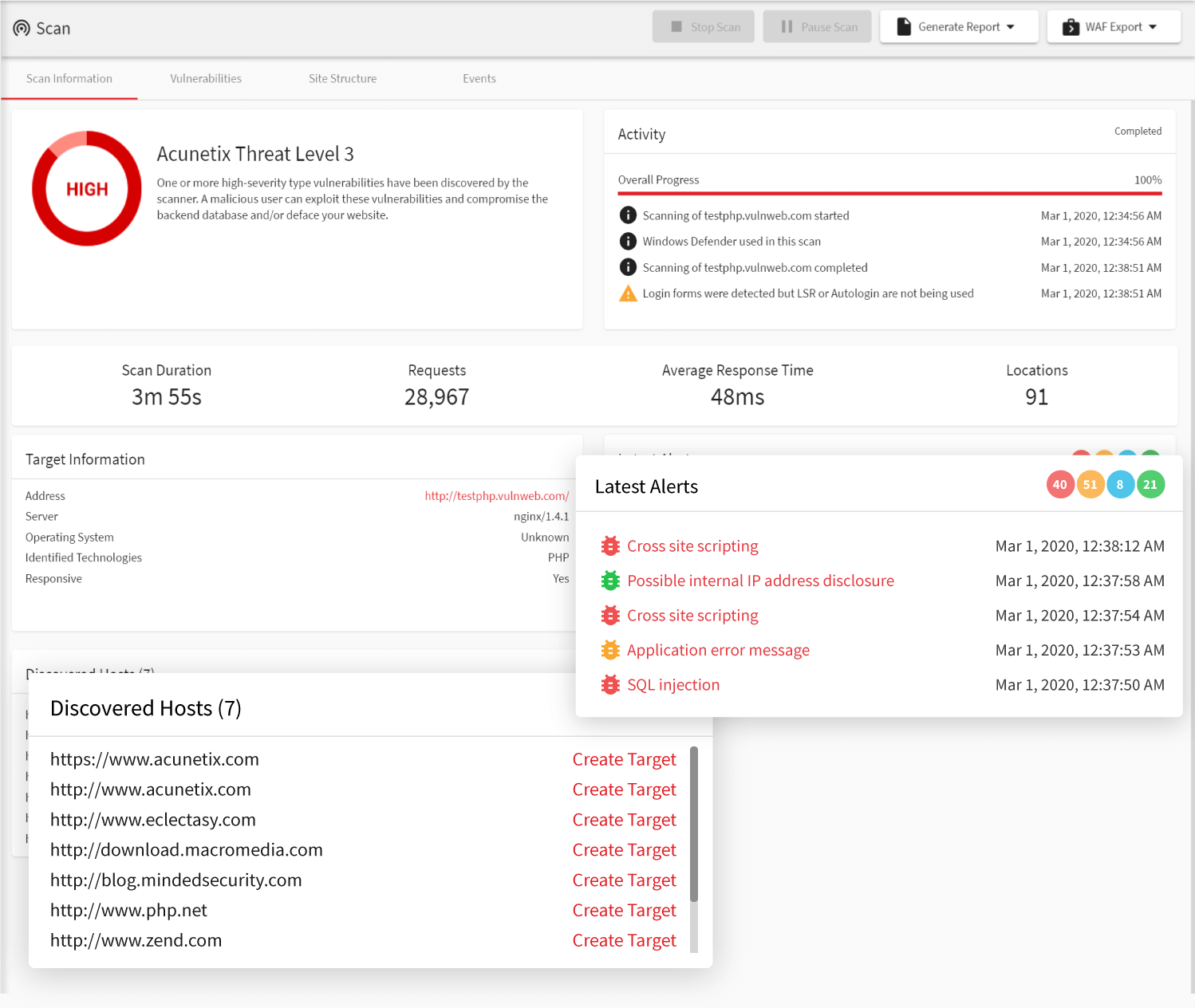
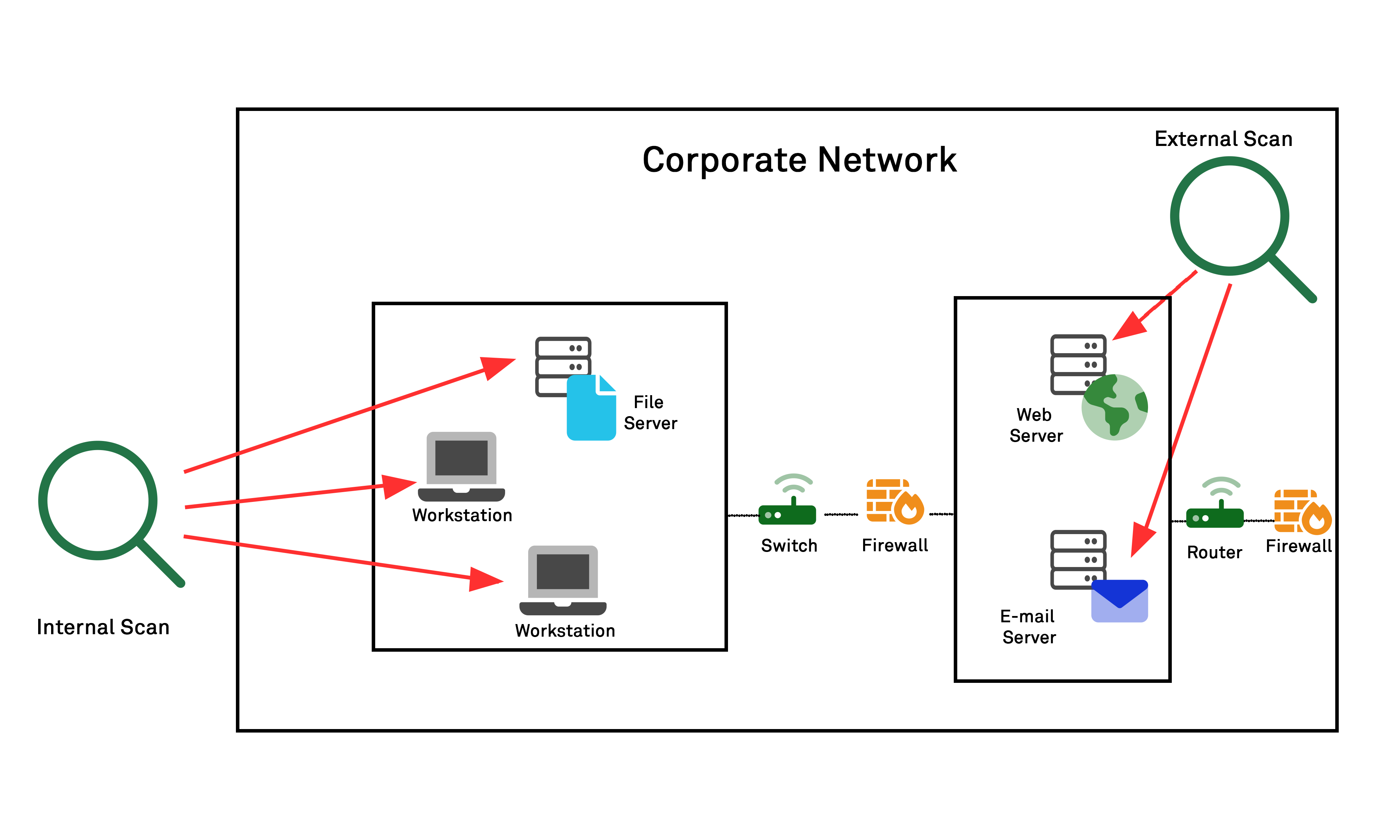
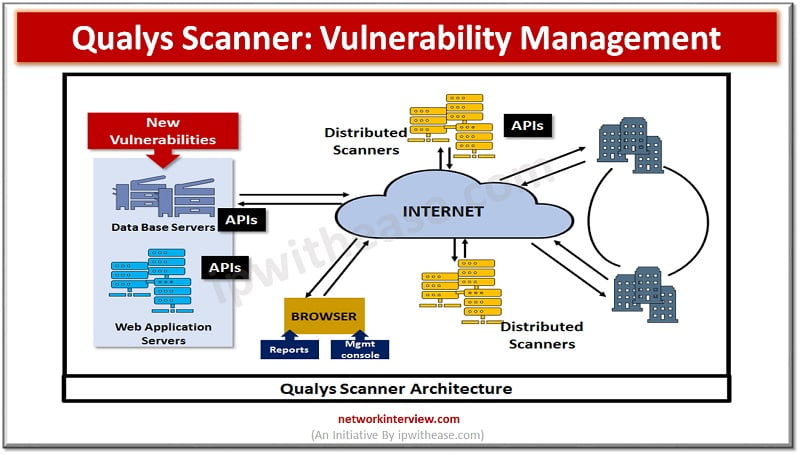
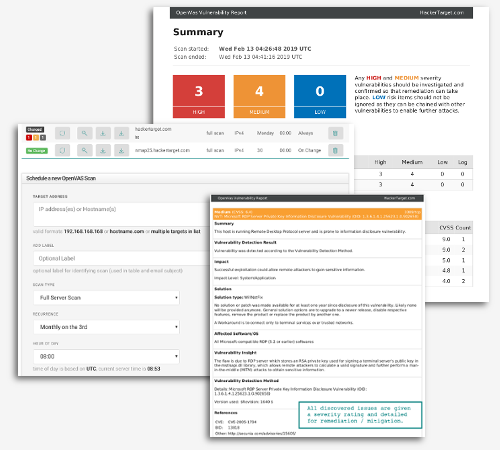
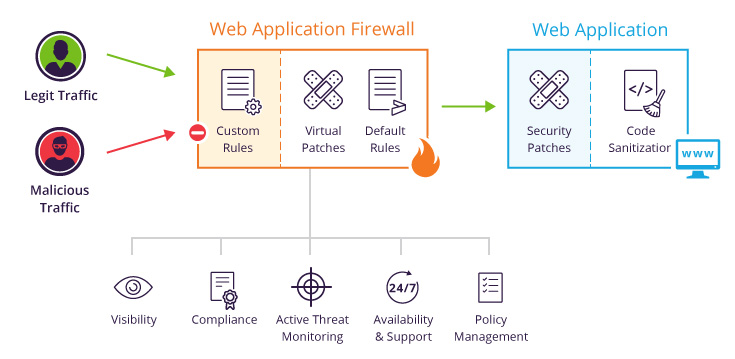
How to Configure NetScaler Application Firewall Signatures Protection Based on Vulnerability Scan Result of QualysGuard
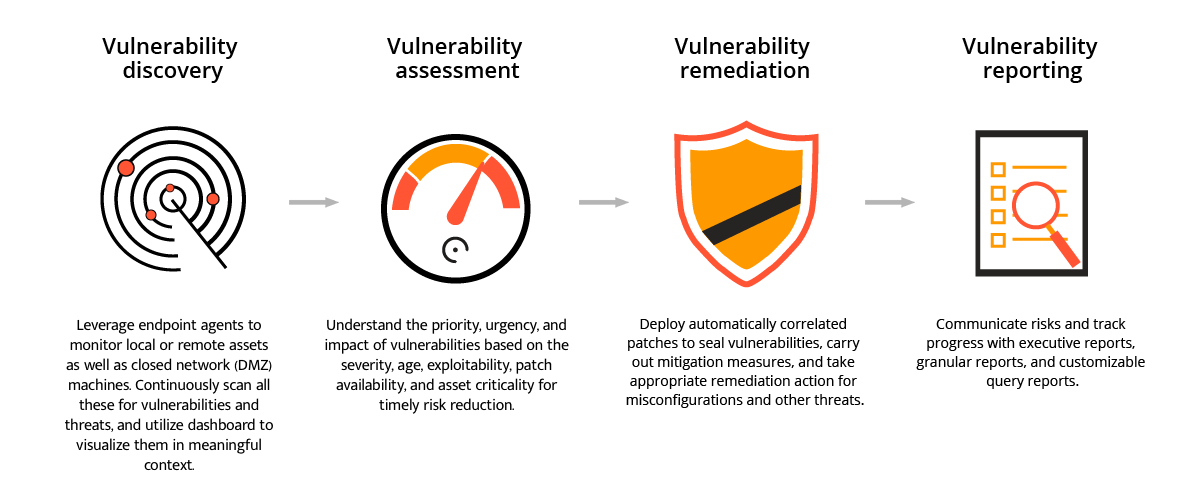
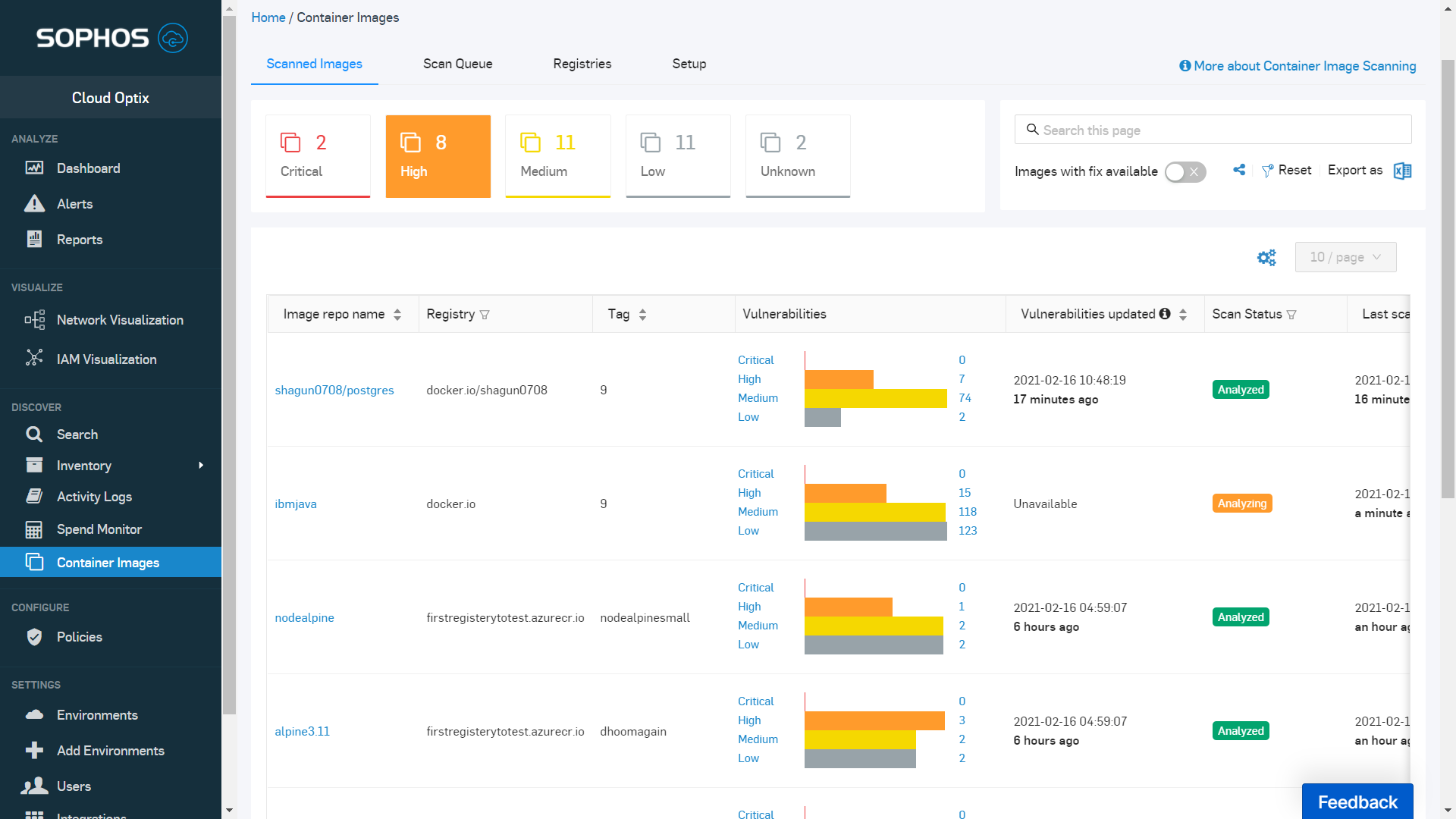
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus

Premium Vector | Cyber or web security online service or platform set. digital data protection and database safety. online course, forum, firewall, vulnerability scanner. flat vector illustration